
This article is about File System Permissions, or File Access Permissions. If you are already familiar with File System permissions, I still recommend that you read the section titles of this article to make sure that you are aware of what permissions your blog-files should have. If you are not familiar with the term File System Permissions, I strongly suggest to bookmark this article and evaluate your files on the server using the tips provided below.
Why is it important to know the access permissions of your server files?
We need to keep our websites protected from malicious attacks. We do not want our blog to be down in a fine morning because it was attacked either by a hacker or by a plugin that we installed without realizing that it may change the files and act fishy.
Installing a security plugin is an option to protect a blog to some degree. Additionally, we can purchase security add-ons from hosting providers to protect our websites. I feel that we still should establish the basic understanding of security at least to confirm that what we pay for really works.
Basic security comes from the file system of the hosting server itself, regardless of what security plugins we install, or what add-ons we purchase. Whether anyone will be able to read, change, or execute the files we have on the server is controlled through the File System Permissions.
All blogging jargons were new to me a few years ago. I want to make sure that the terminology I am using is crystal clear to the reader. By the word “server”, I mean the computer that is hosting the files and the database of your website. It is commonly called the hosting site. Some examples are BlueHost, SiteGround, JustHost, or whatever hosting site you are using. In this article, I use the terms “server” and “hosting site” interchangeably. All your blog-files are stored on the server. I assume that you are using WordPress to run your blog. All the WordPress files are stored on the server too.
It is important to know about access permissions because with incorrect file permissions your website becomes vulnerable to malicious attacks.
Examples of malicious attacks
You might think that the only reason for a malicious attack is to steal information. We thought so too. Recently, after an attack, we came to realize that the goals of attacks can be something quite unexpected, such as inserting backlinks and redirecting Google crawler to other sites of attacker’s choice.
Some attacks are such that you or your readers will not have any clue that the site has been hacked. Secretly your site would look different in the eyes of Google if Google really has eyes ? and eyebrows. Anyway, what I meant is — you will not notice that your site has been hacked because your site will load just fine to you and your readers. However, the site will load differently to Google crawler.
With such attacks, your site will lose Google ranking and no one will see your content in Google search results because Google really was not able to read the content of your blog; rather Google read whatever the hacker provided.
I think this is one of the most dangerous types of attacks of the modern age, given that many businesses depend on the organic traffic derived from the Google search engine.
Many family blogs, mom blogs, and parenting blogs rely on traffic from social media. The blog owners may not examine what is happening with organic traffic. They might never notice that their blogs have been hacked because the hacker secretly presented different content to Google crawler, or redirect the Google crawler somewhere else.
A few days ago, we figured out such an attack on our website. We resolved the issue by studying and tweaking file access permissions. On the way, we figured out a few crucial items. Such as, the default WordPress installation does not set up your website with the most secure file permissions.
This article provides a few basic tips on how to change the default file permissions of your self-hosted self-managed blog to more secure file permissions.
Let’s start. Preliminaries about file access permissions
I assume you use cPanel on your hosting site. I also assume you use File Manager from cPanel to take a look at your files time to time. Our assumptions are boundless — I already assumed that you use WordPress. That means, you have a WordPress installation probably under the folder named public_html.
Here is the complete path where you have your website files (unless it was done differently during the creation of your account):
Practically, the folder public_html contains your blog. No file or directory under public_html should have 0777 access permission. 0777 permission on a file means anyone can read, write, and change the file. You do not want the world to write on your website files.
(Please bear with me a few more minutes. I will explain how to change the permissions.)
The most openhearted access you can give is 0755, which means only you can write and everyone else can read and execute but cannot change the files. In practice, I do not even use 0755 for any file under public_html.
What file permissions do I use for WordPress files?
For any file under the public_html folder, I use file permission 0644, which means I can read the file and write on it; anyone else can read only. Any directory under public_html can have 0755 access, which indicates that you can do whatever you want but others can only read and execute but cannot write on the directory.
I use exceptions for two files in public_html: index.php and wp-config.php. Access permissions of these two files are explained below.
File permission for index.php
As you may know, index.php is the first file that the server executes when someone browses your site. It may seem, visitors of our blog need to read and execute the index.php file. What seems is not correct. When someone visits your site, the server computer will execute the index.php file and show the output to the visitor. Therefore, no one in this world needs to see your index.php file. Only the server computer needs to read and execute the file.
I change the permission of index.php to 0400, which means only I can read it and no one else can even see it.
Note that the server computer has the ability to execute the index.php file regardless of the access permission you give. Therefore, your site will still work fine if you use 0400. Permission 0400 for index.php of my website is working fine. I am pretty sure (99.99%) the most restricted permission 0400 will work for yours too.
If 0400 does not work for you, then use 0440, which is slightly less restricted but still strict enough NOT to allow the world to see or change or execute the file directly. 0440 adds read access to “Group”, where a group may refer to a set of programs on the server or people you allow to see the files.
We must change the default access permission of wp-config.php
The first thing I would do after installation of any WordPress site is change the permission of wp-config.php (and index.php) under the public_html directory. The default permission is generally 0644 for wp-config.php. 0644 means you can read and write; the world can only see. That is, wp-config.php can be seen by anyone by default.
Unfortunately, wp-config.php contains some vital information that you probably do not want to make public. For example, it contains the database password and some authentication keys. Fortunately, no one needs to see this file, other than you or the people in the hosting service.
I generally change the permission of the wp-config.php file to 0400, which is (again) — I can read the file and everyone else can neither read nor write nor execute the file. If anytime, I need to edit the file, I would make the permission 600, which grants write-permission to myself. After editing, I would change the permission back to 0400. We rarely need to change this file. Same goes for index.php. If you need to edit something on index.php, change the permission to 600, edit the file, save it, change the permission back to 0400.
How to change file permissions
In the File Manager of cPanel, the right-most column (in my File Manager) shows the file access permission. Please take a look at the picture below. There are four-digit numbers in the right-most column. These are the permissions. Select a file, right clink, then select “Change Permission” from the list of operations.
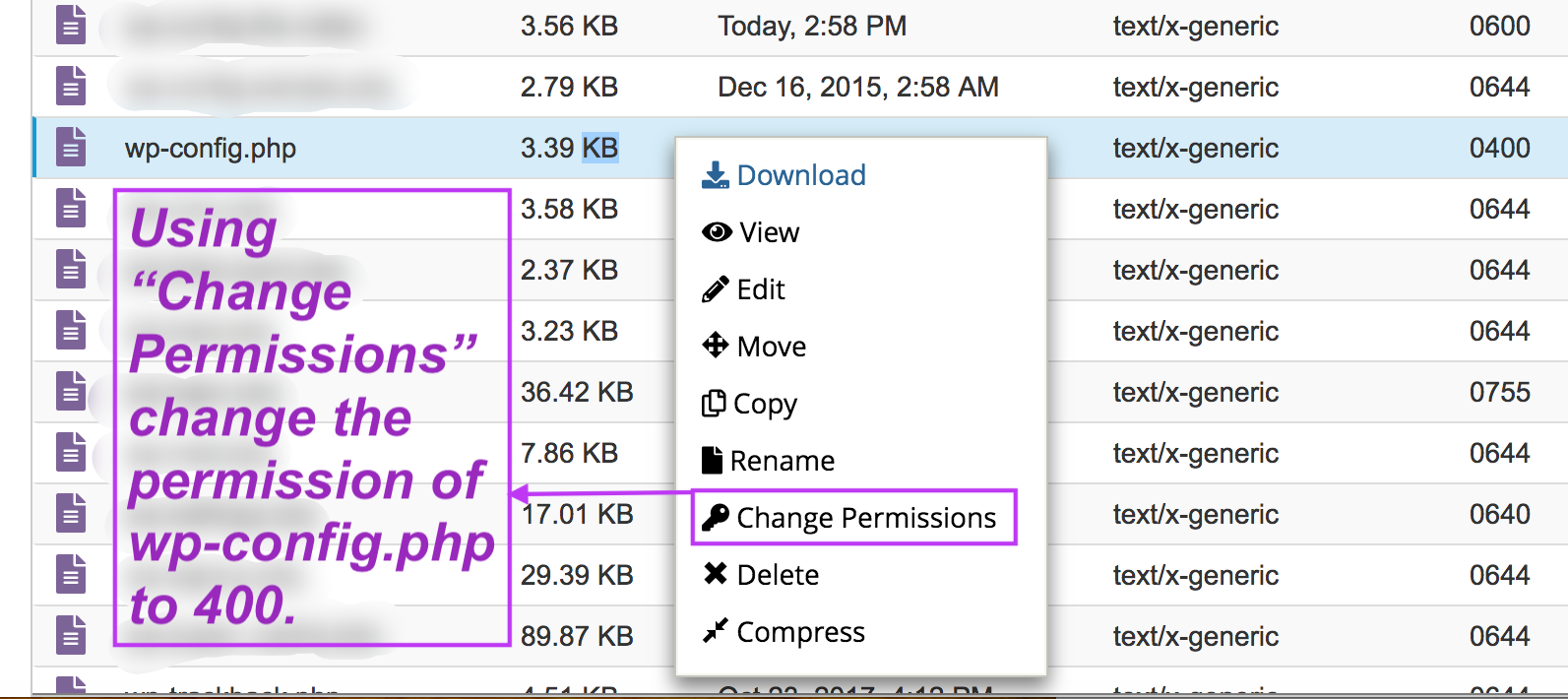
A window like the following one, containing a table of checkboxes, will pop up. Change the file permission to a desired four-digit number by checking or unchecking the boxes. The “User” column refers to you. The “Group” column refers to people or programs that have certain rights to your files. The “World” column refers to people all over the internet. The rows are pretty self-explanatory (Read, Write, Execute).
Check or uncheck the cells to get the desired four-digit number at the bottom of the table. Then press the “Change Permissions” button.
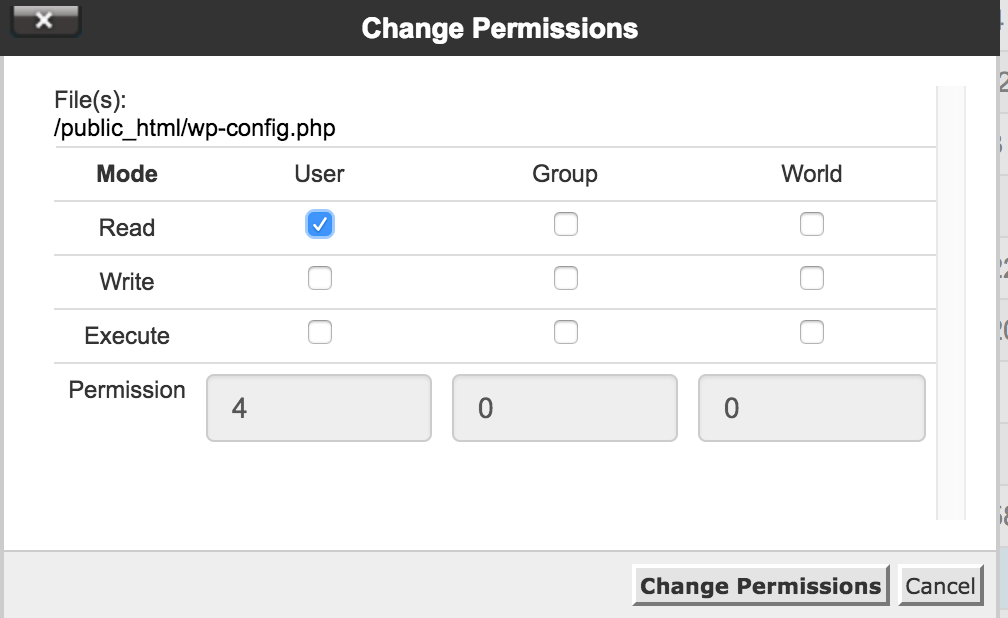
I change the permissions of index.php and wp-config.php to 0400, which is the most secure one.
Aside from file access permissions, know your index.php file
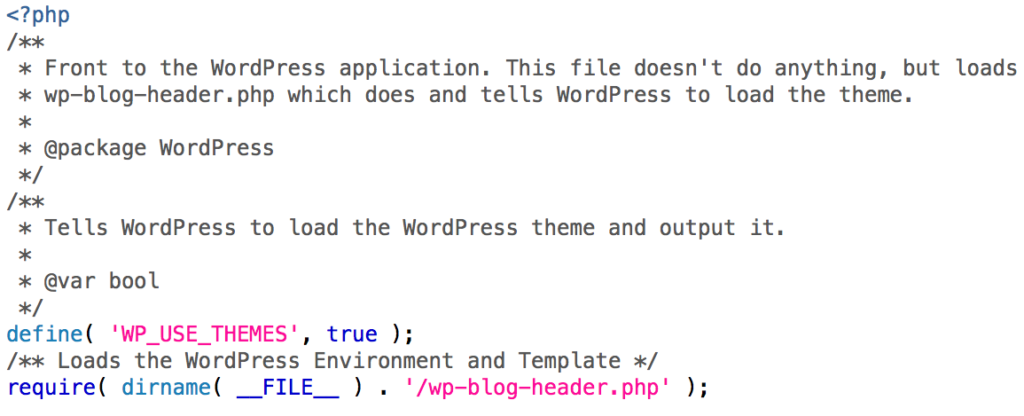
A fresh WordPress index.php file should look like the following, or something similar:
Any code more than the above is fishy. A few days ago, when the attack happened on our site, I found a little less than 100 additional lines in the index.php file. The website was running just fine. I noticed that Google Search Console was receiving different content than what it should for each of my posts. Luckily, I was able to figure out that the index.php file was corrupted.
I deleted the redundant part and everything was fixed. The next day the redundant part came back. ?
I called my hosting company. They said that nothing from their side is responsible for this. It might be something within my WordPress site. I guessed, a plugin corrupted it.
This time, after deleting the redundant part from index.php, I changed its file permission to 0400. After that, the redundant part did not come back anymore.
Anyway, the basic idea is — know what is normal in the index.php file. It will help you figure out what is not normal.
Learn about your wp-config.php file
A standard wp-config.php sample can be found here: https://github.com/WordPress/WordPress/blob/master/wp-config-sample.php
As I said earlier, wp-config.php contains crucial information. As provided in WordPress.org documentation, the Database credentials (DB_USER, DB_PASSWORD, etc.) will be written here. We do not want to make the file public because making it readable to others increases the risk of attacks. I prefer to change the permission to 0400, as said earlier.
Concluding remarks
File Access Permissions or File System Permissions are one of the easiest things we can do ourselves. Setting them up properly makes a blog more secure. Please go ahead and change the access permissions of the files if you did not change your default file permissions after you created your blog. The change will improve the security of your blog.
Let us know if you have questions. Have a wonderful week!
From a Family Blog: Settle in El Paso
Other posts related to blogging
Subscribe to receive notifications on our new posts.







Comments
Facebook Comments